Being in the utilities sector comes with its host of complex challenges — climate disasters, geopolitics, changes in supply and demand, and fast-paced technology updates. But out of all those factors, cybersecurity for energy and utilities continues to be one of the most pressing and most difficult risks for companies to keep up with.
That’s why it’s crucial to keep your control room up to date and also design it in a way to mitigate cybersecurity threats. It can make a difference in your team making it through or failing in the face of an attack.
First, we’ll look at current threats around cybersecurity in the utilities industry to help you identify the risks for your organization before you design or renovate your control space. Then we’ll look at 4 steps you can take to make sure your facility is prepared before starting this type of project.
Current Cybersecurity Threats Facing Energy & Utility Companies
Unfortunately, the hardest aspect of cybersecurity threats is that it’s challenging to plan for the unexpected. Bad actors are always figuring out new ways of causing destruction just as fast as new technologies are being developed. Plus, some hackers have political support behind their malicious operations targeting utilities or other crucial infrastructures worldwide.
While it’s hard to say exactly what form the next cybersecurity attacks will take, knowing your high-risk areas can help you prepare and stay vigilant.
Cyber Risks for Energy
Depending on where your organization falls in the operation chain, there are unique risks for generation, transmission, distribution, or network facilities. They can span the gap of disrupting generation, interrupting service connections, or stealing sensitive customer information.
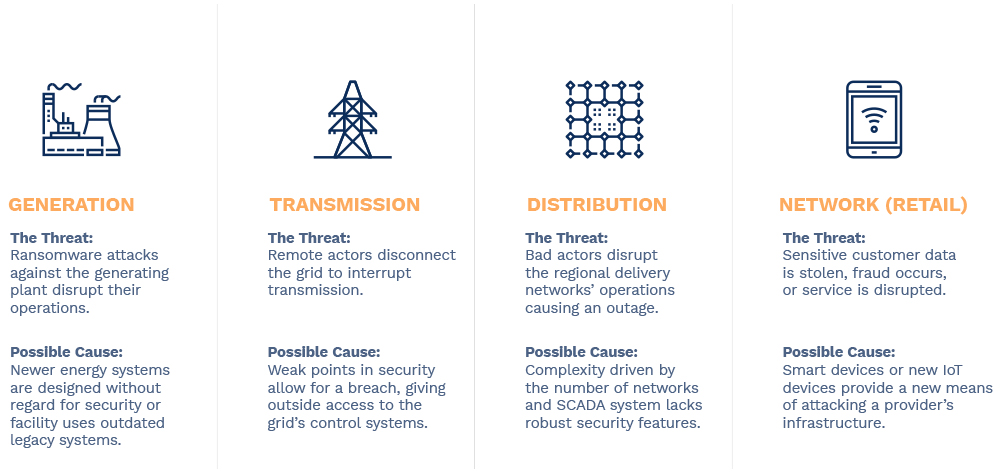
Cyber Risks for Utilities
Similar to the energy sector, other utilities operations (eg., water, sewage, gas, etc.) face some of the same risks. They include (and are not limited to):
- Ransom attacks that disrupt equipment and operations
- Sophisticated spearfishing attacks among organizations to get access to networks
- Extorting outdated operating systems and software
- Exploiting internet-connected devices
While the tools are different, there is a pattern in the way hackers are disrupting utilities. Having the right control room structure is key to having an agile response to cybersecurity attacks. From the technology visualizing data to the situational awareness software in use, it’s important to stay vigilant for vulnerabilities and invest in your technology infrastructure to keep it up to date.
And if you’re in the process of updating or designing a command center, it’s the perfect opportunity to strengthen security to meet current demands. If you’re beginning a control room design project, here are 4 practical steps to take to ensure you have strong cybersecurity controls in place.
Step 1: Implement Or Upgrade Your Threat Intelligence
As an organization, it’s essential to subscribe to a threat intelligence service so you have the most up-to-date information on the global landscape. Cyber risk is nothing new — it’s been an ongoing problem. But the tactics change quickly and having outside intelligence can help you continue refining your cybersecurity implementation plan to reduce vulnerabilities.
Since developments move fast, make sure you follow credible cyber news sources as well, to keep abreast of breaking happenings. It’s also a good idea to look to cybersecurity experts who are sharing relevant content.
You can also visit the Cybersecurity & Infrastructure Security Agency (CISA) online to get up-to-date information. They partner with both the government and industries to share pertinent information and ensure the U.S. is able to stay secure against cyber attacks.
Use Cyber Intelligence In Your Planning
Apart from implementing cyber intelligence reactively in your command center, consider taking it one step further. Use intelligence from different sources — vendors, services, the government — and let it also play a role in all business developments.
For example, if you’re designing a new control room, make sure the folks collecting and analyzing that data have a chance to review the design strategy and plans in place. With their expertise in cybersecurity for energy and utilities, they may be able to pinpoint flaws that put your center at risk before it’s even completed.
Step 2: Revisit & Secure Your Technology Operating Model
With the rapid developments of technology, we are seeing IT (information technology) and OT (operational technology) converge, when in the past they were very much separate. And there is a benefit to merging the two.
Especially in a control room environment, having those systems connected instead of siloed can lead to better data visualization and comprehensive control to help make and execute informed decisions. The key is to make sure that both IT and OT systems are being monitored and that with the convergence, there are no new vulnerabilities as the two merge.
One of the key issues companies are facing with this shift is a lack of clarity around who is responsible for monitoring IT vs OT. So make sure you have it spelled out who in the business line is accountable for both.
Step 3: Create Or Update Your Cybersecurity Implementation Plan
Having a good cybersecurity implementation plan in place is the key to having a strong foundation. Whether you’re going into building a new control room or redesigning one, make sure you have this plan spelled out and ready to use as you undergo this project.
Your cybersecurity plan should rely on the following framework:
Phase 1: Assess & Develop
Review, audit, and refine the structure of the organization. How are you collecting cyber intelligence? Who is responsible for threats? Are you complying with national and international security standards?
Phase 2: Update & Document Processes
Internally, develop all the legislative and technical processes.
- Account for both IT and OT systems.
- Build a vetting process for any technologies (eg., video walls, software, etc.) being used.
- Invest or update your security information and event management (SIEM) solution and SCADA system.
- Clarify which parts of the business line are responsible for monitoring / handling different types of suspicious activity.
- Create a cybersecurity incident response plan in this preventative implementation plan.
You can’t be too specific in this stage. Layout everything clearly and make sure it’s documented. A holistic plan is the best way to stay protected.
Phase 3: Train Every Employee
Employees that are unaware of best cyber practices are the most dangerous. Train everyone — not just in the control center or cyber team, but across the entire organization.
Each employee should be aware of the role they play and understand how to keep the company safe. (Even down to the person cleaning the control room.) That way no bad actors find access to harm your command center through an unsuspecting employee.
Phase 4: Always Make Improvements
It’s wise to continue auditing your cybersecurity plan on a continual basis to ensure it’s able to keep up with recent developments. Make sure you advocate for the budgets you need to keep your plan robust. Tweak it as new issues rise up and invest in your cyber team. And always give clear communication around those improvements and changes.
Step 4: Vet Your Partner’s Experience
As you search for a partner to help you with your command center design, look for someone with experience designing control rooms in the utilities industry. They’re already familiar with cybersecurity for energy and utilities and the current challenges and risks. Plus they’ll have an understanding of the standards you need to comply with.
Because of that, your partner will be able to offer you design opportunities that can support your cybersecurity implementation plan. Plus, they may be able to offer an outsider’s perspective on how the setup of your control room can be improved to mitigate risk.
At Mauell, you can have peace of mind that information regarding your control room design will be handled appropriately in keeping with common cybersecurity requirements (NIST 800 – 171, CMMC 2.0). Throughout our process, our team ensures that all photos and projects will not be released to non-critical personnel.
When looking at your cybersecurity implementation plan, our team also looks to see if any assets we’re providing will be touching your corporate network or SCADA and control networks. If so, we approach those assets with an increased level of security and will quarantine them first before allowing them to be deployed in your control room.